Report #THR20101217A
Release Date: 17.12.2010
Executive Summary
The hacktivist who goes by the handle “th3j35t3r” has been carrying out denial of service (DoS) attacks against suspected jihadist websites since he showed up on the hacktavism scene on January 1, 2010. He uses a DoS tool called XerXes that he claims to be the sole author of. He also claims to be “an ex-soldier with a rather famous unit” and to have served two tours of duty as an airborne combat trooper “in (and around) Afghanistan amongst other places”. He says he is between 31-49 years old.
He recently carried out a DoS attack against wikileaks.org, which generated quite a bit of media attention. He is now a declared target of Anonymous, some of whom’s members believe he is a Robin Jackson of Helena, Montana, a 49-year-old employee of the State of Montana who goes by the online handle of “rjacksix”. But while rjacksix has publicly claimed that he and th3j35t3r “have worked together” and share “operational details”, it is unlikely that Robin Jackson is th3j35t3r.
The involvement of rjacksix and others, however, shows that th3j35t3r is not the “lone wolf” operator he has claimed to be and receives operations support from civilians like rjacksix. Some have suggested that th3j35t3r might also receive some level of support from operatives within the U.S. intelligence community. While there is no hard evidence that th3j35t3r has assistance from the U.S. Government–an assertion that he expressly denies–it is unlikely that no one inside the U.S. intelligence community, the Department of Defense, or law enforcement has no knowledge as to th3j35t3r’s true identity given his stated military background and the fact that he posses such a demonstrably powerful and effective cyber-weapon as XerXes.
Some have gone as far as to suggest that th3j35t3r is not an individual at all, but a persona created as a front for a secret government program that carries out unattributable cyber-attacks. While this is not beyond the realm of possibility, there is no hard evidence to support this far-fetched claim, which gets cut to pieces when pressed against the sharp blade of Occam’s razor.
The identity of th3j35t3r as an individual, a group, a secret government program, or otherwise remains unknown and he is “crack on”, as he has said, with his DoS campaign against jihadist websites.
An Ex-Soldier
th3j35t3r (The Jester) is a self-proclaimed “hacktivist for good” who has taken down numerous jihadist websites and, most recently, wikileaks.org using a denial-of-service (DoS) attack. Although there has been much speculation, th3j35t3r’s identity has not been conclusively determined and confirmed. In an email exchange with Richard Stiennon, author of Surviving Cyberwar, in January 2010, th3j35t3r claimed he is ex-military.
“I am an ex-soldier with a rather famous unit, country purposely not specified,” wrote th3j35t3r. “I was involved with supporting Special Forces, I have served in (and around) Afghanistan amongst other places.”
In a November 30, 2010 interview with ABC News, th3j35t3r said that he is under 50 years of age and over 30. He said that he began coding at the age of 10 because he was “thirsty for knowledge about how computers worked, and fascinated by the fact that just a guy and a keyboard might make a difference to something.” thj35t3r also said that he was “always drawn to applying myself within the military,” and that he served twice as an airborne frontline combat trooper.
Assuming that what th3j35t3r said is true, we can only speculate about what branch/unit th3j35t3r served in. Although th3j35t3r did not specify the country and unit, it is likely that he was with either the United States Army Special Forces or United States Army Rangers. Specifically, the 75th Ranger Regiment has been deployed in Afghanistan (Operation Enduring Freedom) and in Iraq (Operation Iraqi Freedom).
The only other “special forces” units known to have carried out operations in Afghanistan were the Spetsnaz during the Soviet war in Afghanistan (1979-1989) and, more recently, the United Kingdom Special Forces (UKSF).
Given th3j35t3r’s proven cyber skills and prowess, it is also plausible–but in no way substantiated–that he was (or still is) in some way connected with one of the various cyber command units that are now under the recently created United States Cyber Command (USCYBERCOM), which was officially activated May 21, 2010 and reached “full operational capability” on November 3, 2010. Again this is only speculation.
th3j35t3r sometimes uses “hooah” (and variations) in his Twitter posts, further suggesting that he is ex-U.S. military. The term “hooah” and variations such as the USMC “oorah” are common throughout the various branches of the U.S. military.
In addition to using the U.S. military term “hooah”, th3j35t3r also often uses the phrase “tango down” in his Twitter announcements about websites that he has taken down with a DoS attack. “Tango down” is a special forces military term for having eliminated a terrorist, according to Chandler’s Watch, a radio show and accompanying website run by two Marines.
th3j35t3r has stated that he takes operations security (OPSEC) “very seriously”. This further seems to support his claim that he is ex-military and has operations field experience. At a minimum, it separates him from “skiddies” as well as those who are currently carrying out traditional DDoS attacks against websites and/or engaging in site defacement, which is something that th3j35t3r claims he does not do:
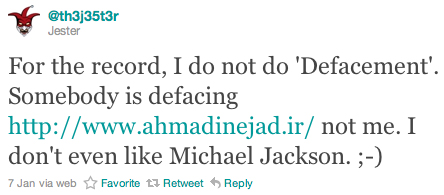
Source: twitter.com/th3j35t3r
“Skiddie”, which is short for “script kiddie”, is a derogatory term used to describe those who use scripts or programs developed by others to attack computer systems and networks and deface websites. Based on th3j35t3r’s hackography, however, calling him a “skiddie” is merely juvenile name-calling.
th3j35t3r has been carrying out systematic cyber-attacks against suspected jihadist website targets using his own DoS utility since he appeared on the hacktivism scene on January 1, 2010. His stated purpose for these ongoing cyber-attacks is to disrupt terrorists from using the Internet as a means of recruiting and coordinating:
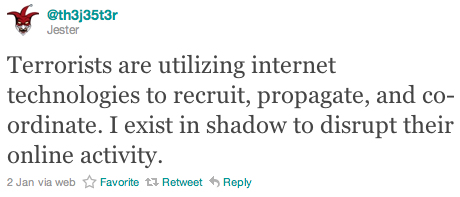
Source: twitter.com/th3j35t3r
In addition to his stated practical reason of causing disruption to suspected jihadist websites, th3j35t3r has made statements that suggest he operates with the moral foundation of utilitarianism as evidenced by one of his early Twitter postings:

Source: twitter.com/th3j35t3r
Weapons of Mass Disruption: The XerXes Attack Platform
th3j35t3r uses a DoS “attack platform” called XerXes. The “attack platform” concept comes from th3j35t3r himself. Beginning on November 16, 2010, his Twitter postings were flagged as being published “via XerXes Attack Platform”.
In a February 2010 interview with Infosecisland.com Managing Editor Anthony M. Freed, th3j35t3r stated that XerXes started with “a little script I wrote a while back to harden-test servers.”
“I modified this script, and it was just a nasty script, very cumbersome,” the th3j35t3r told Freed. “When I realized the extent of the jihad online recruiting and co-ordination involvement (much later), I realized I could turn this script into a weapon.”
XerXes is a denial of service (DoS) software platform. It is important to distinguish it from a distributed denial of service (DDoS) attack. In the DDoS attack model, many computers are used to send simultaneous and repeated requests to the webserver hosting a particular website. In most cases, this collection of remote computers are computers that have been compromised through malware injection and/or exploitation of unpatched security holes and/or zero-day security exploits. In many cases, the owners of compromised and exploited computer systems are unaware that those systems are participating members of a botnet. In a DDoS attack, the attacker activates the compromised computer systems that have been corralled into the botnet and uses them to make repeated requests to the webserver that hosts the target website until the server becomes overwhelmed and can no longer accept legitimate inbound HTTP requests.
XerXes is different. According to th3j35t3r, it does not require a botnet nor comparable vast computing resources in order to carry out a successful attack against a specified target.
“There is nothing ‘distributed’ about this,” th3j35t3r said. “It is possible with very low bandwidth and a single low-spec Linux machine.”
According to th3j35t3r, XerXes “does not require a botnet, zombie PC’s or other people’s bandwidth in order to successfully pull down a site.” The veracity and effectiveness of XerXes has been confirmed and th3j35t3r has made publicly available two video demos of DoS attacks using XerXes.
“Once a single attacking machine running XerXeS has smacked down a box, it’s down, there is no need for thousands of machines,” th3j35t3r told Freed in February. He added that the attack only affects the intended target.
“Many people worry about the nodes between me and the target,” th3j35t3r said. “This technique affects nobody but the intended target. All intermediaries remain unaffected.”
th3j35t3r claims to have independently developed XerXes without any government sponsorship or involvement. When asked in a June 2010 interview with Welt Online if he was “supported in any way by Western governments, intelligence agencies or anybody who is also fighting Jihadi propaganda”, th3j35t3r responded, “At this time I work completely alone, and have no ties or affiliations with any government entities.”
“Lone wolves work faster, eat more and are harder to track and capture,” he added.
A Sheep in (Lone) Wolf’s Clothing?
If th3j35t3r is indeed the “lone wolf” he claims to be, he’s accomplished a lot for one person this past year: writing and testing code for his DoS attack platform (which includes a GUI), researching and assessing Arabic-language websites for targeting and attack, and being his own publicist to mention a few. All of this would be quite achievable for an individual with the right combination of skill-sets, experience, time, and resources.
Whether or not th3j35t3r has direct or tacit support from the U.S. intelligence community, he likely has support from someone. Up until the wikileaks.org attack, the websites he has taken down have been Arabic-language “jihadist” websites.
The grammatical structure of Arabic is very different from English (as well as other Indo-European languages). Online translation software such as Google Translate or Babel Fish do not do a good job of translating Arabic into comprehensive English. At a minimum, one must have an intermediate understanding of Arabic grammar and the nuances of its triliteral root system in order to achieve a coherent and useful translation in English.
Due to this fact, there are only several possibilities: 1) th3j35t3r has at least intermediate Arabic-language skills, 2) he has help from someone who does (government or civilian), 3) he relies on only a handful of easily translated keywords and/or phrases to determine that a website or forum is “jihadist” in nature and should therefore be targeted.
In a January 2, 2010 posting on Twitter, th3j35t3r wrote:

Source: twitter.com/th3j35t3r
Analysis of that translation by an Arabic linguist working on behalf of T3h Her0d07u5 Rep0r7, has determined that it was a machine-generated translation and not that of a human with at least intermediate Arabic-language skills.
In his interview with Welt Online, th3j35t3r stated, “many followers on twitter have passed leads on to me, which I then vet to ensure the site poses a threat before it makes it onto the hit-list.”
One of th3j35t3r’s followers on Twitter asked him directly how he found the sites he targets:
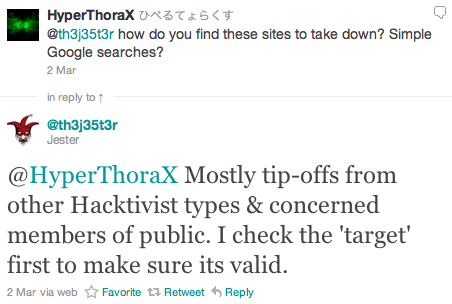
Source: twitter.com/th3j35t3r
Based on the information we have at this time, there is no compelling evidence that th3j35t3r acting as a lone operative has the Arabic-language skills one would need in order to thoroughly and accurately vet a suspected jihadist website to “ensure the site posses a threat before [being placed] onto the hit-list.”
The Anonymous Hunt for th3j35t3r
“Often the surest way to convey misinformation is to tell the strict truth.”
– Mark Twain, quoted by th3j35t3r in a December 9 blog posting.
Who is th3j35t3r? This conundrum has recently been the focus of Anonymous participants who have sought to determine and expose th3j35t3r’s true identity. Interestingly, the occurrence and nature of these efforts were made public by th3j35t3r himself who recently published a lengthy excerpt from an IRC session (#AnonymousDown) with a date/time stamp of Fri Dec 10 15:38:58 2010. It was unclear whether th3j35t3r was a participant in the session under an alias or whether he was a silent observer or gained access to the session log by other means. He recently boasted on Twitter that he has “eyes on” inside of Anonymous:

Source: twitter.com/th3j35t3r
The topic of the IRC session was, “Let’s find the guys that are trying to stop us. AnonymousDown: http://twitter.com/AnonymousDown – http://www.stumbleupon.com/stumbler/AnonymousDown/. th3j35t3r: http://twitter.com/th3j35t3r – http://www.xfire.com/profile/th3j35t3r/ – http://th3j35t3r.wordpress.com”.
The entire session log snippet is 484 lines in length. What follows is a pieced together narrative of key excerpts from the IRC session transcript in which participants speculated about th3j35t3r’s true identity:
Thatoneguy: “Who’s the jester?”
AsD: “nothing”
AsD: “forget him”
@Cyberpolice: “We have a name, but not confirmed.”
@Cyberpolice: “Rusty Schackelford”
@Cyberpolice: “lol”
[Rusty Shackleford is an alias for the fictional character of Dale Gribble on the animation series King of the Hill.]
Fr0stii: “wow some fuckin kid tryin to jump on the bandwagon”
Beagollum: “according to his twitter not just a kid”
Beagollum: “some anti-jihad, US-nationalist”
@Cyberpolice: “yea he’s attacking jihad shit”
@Cyberpolice: “And us”
@Cyberpolice: “He’s using XerXes”
CrazyKlompjes: “he could be ofcourse a forefront for the government”
Ap3X: “There are enough leads that Jester = 1 person”
Ap3X: “1 day ago we tracked down a guy who seems to be him”
Ap3X: “we have no proof though”
Beagollum: “what info did you got?”
Ap3X: “ill search it up for you”
Ap3X: “jester seems to be -> rjacksix”
@Cyberpolice: “rjacksix?”
Ap3X: “rjacksix = has a hacking website too”
Ap3X: “and writes alot about Jester”
Ap3X: “Jester speaks English And russian”
@Cyberpolice: “rjacksix = Robin Jackson”
Ap3X: “exactly”
Ap3X: “rjacksix states on his linkedin that he speaks english and russian”
bada: “rjacksix isnt the jester”
bada: “i looked into it heavily”
Ap3X: “rjacksix works for the gov.”
bada: “similar interests, similar everything”
bada: “but not him”
bada: “in my opinion”
@Cyberpolice: “Why not?”
bada: “i could be wrong though”
@Cyberpolice: “No one is sure in here”
Ap3X: “Well all leads go to rjacksix”
bada: “i forget exactly why i ruled him out”
bada: “it was like a week ago”
Beagollum: “if he is jester, he is weird”
Thatoneguy: “could it be real hackers from 2600?”
Ap3X: he is wierd
@Cyberpolice: “Well most people only use 1 username”
Beagollum: “indeed”
Ap3X: “1 day ago we traced all info on”
Ap3X: “rjacksix”
Ap3X: “we even got his home adres & phone nmber”
@Cyberpolice: “fuck”
Ap3X: “Point is we have no proof”
@Cyberpolice: “Ap3X Yea you can’t act without proof”
Ap3X: “exactly”
Ap3X: “only thing we can is phone this guy and say: Hello jester”
Ap3X: “see how he respons”
@Cyberpolice: “Jester whats up man? Wanna hang out?”
Ap3X: “hellow Jester, we know your there”
Beagollum: “something doesn’t add up”
Ap3X: “if the man doesnt know well then its not him”
@Cyberpolice: “Just ask if Jesters home”
Fr0stii: “I’m in the US what is his number?”
Ap3X: “remeber it might NOW be him”
Fr0stii: “I know…”
Ap3X: “just ask if Jester is home”
Fr0stii: “I’m not asking for jester…. most dont call me and ask for frostii ahaha”
Fr0stii: sec brb
Beagollum: “Frostii, ask for Rusty Shackelford”
@Cyberpolice: “I bet his mom will pick up the phone”
Fr0stii: “answering machine ‘hi you have reached the jacksons plz leave a msg after the tone and have a good day'”
@Cyberpolice: “fuck”
Beagollum: “well, atleast it’s a real number”
Fr0stii: “it sounded like a young guy on the answering machine”
@Cyberpolice: “Its all connected somehow”
Ap3X: “point is, we have no 100% proof… just suspicions”
@Cyberpolice: “Yes we need proof”
@Cyberpolice: “We need to find the link between th3j35ter and Jackson”
Fr0stii: “yea I’m trying something now. somehow we have to link this to the miltary background”
Fr0stii: “right ahaha”
Ap3X: “he has a ex mil background”
Ap3X: “there is proof for that already”
Ap3X: “The intrusion of the military into the commercial realm raises immediate Posse Commitatus issues.
[The Posse Comitatus Act prohibits federal military personnel and units of the National Guard under federal authority from acting in a law enforcement capacity within the United States, except where expressly authorized by the Constitution or Congress.]
Ap3X: “If the military isn’t allowed to police the physical world in in the US, why would we think that it was OK for them to do so in the virtual world.”
Ap3X: “I am not some extremist either. I am ex-military and worked in a no-such for quite some time.”
Ap3X: “The question is one we need to address.”
Ap3X: “only way to find out if its jester is to piss him off”
Beagollum: “Jackson was military”
Ap3X: “Started as a Russian Linguist”
Ap3X: “and he speaks russian”
Ap3X: “both facts point to Jester”
Beagollum: “there’s a connection”
Beagollum: “RL-connection”
@Cyberpolice: “Yes there is”
@Cyberpolice: “So are we going to announce that we found th3j35ter?”
Ap3X: “this guy needs to disapear”
Ap3X: “Question is… did we find him?”
Beagollum: “no plubicity until it is proven 100% who he is”
Ap3X: “Agree”
@Cyberpolice: “We just need to confirm that he’s the guy”
But to date, there has been no confirmation–only speculation–as to th3j35t3r’s identity. th3j35t3r has denied being Robin Jackson.
“If you think I am Rusty Shackleford–you fail,” he wrote in his December 10 blog posting. “If you think I am Robin Jackson–you fail again.” Then he added this:
“In conclusion, you should rest assured that you don’t ruffle me at all–I don’t have a single shred of fear induced by yourselves, what I do have are a very particular set of skills; skills I have acquired over a very long career. Skills that make me a nightmare for people like you.”
Members of Anonymous who launched Operation Payback, are now targeting Robin Jackson (who goes by rjacksix online) because they believe that he is th3j35t3r. The following is the poster announcing Anonymous’s targeting of Robin Jackson:

Source: praetorianprefect.com
The following posting by Anonymous provides information for what they have called “Project th3j35t3r”:

Source: praetorianprefect.com
The timestamp on this posting is December 9. The IRC session log in which Anonymous members are discussing and speculating about the identity of th3j35t3r is dated December 10. Based on that disparity, it looks as though Anonymous engaged in “Project th3j35t3r” while still uncertain that th3j35t3r was indeed Robin Jackson.
According to his Linkedin profile, Robin Jackson is the Chief of the Management Services Bureau for the State of Montana. This is confirmed at the State of Montana’s official website, mt.gov.
According to his profile at internetrevolution.com, Robin Jackson (rjacksix), “Started as a Russian Linguist. Learned how to program at Ft. Meade MD (hehe). Left the military and ended up doing SCADA for GE…Currently manage computer programming, technology, budget, leases and other support functions for the Montana Dept. of Labor, Employment Relations Division.”
Jackson’s Linkedin profile does not mention his having been a Russian linguist nor having served in the U.S. military and/or having worked for the NSA. His Linkedin profile does, however, list his specialties as: “Open Source, Linux, PC’s, servers, virtualization, networking, web publishing, web pages, ITIL, technology, technology forecasting”.
In a December 10 Twitter posting, Robin Jackson outrightly denied being th3j35t3r:

Source: twitter.com/rjacksix
And again on December 11:

Source: twitter.com/rjacksix
rjacksix follows th3j35t3r on Twitter. So do 6,546 other people as of December 17, 2010. rjacksix was the 518th follower of th3j35t3r. rjacksix has 195 current followers on Twitter. His 10th follower was th3j35t3r, who currently only follows 67 people on Twitter.
According to whendidyoujointwitter.com, rjacksix joined Twitter on February 17, 2009 and th3j35t3r joined on December 19, 2009:

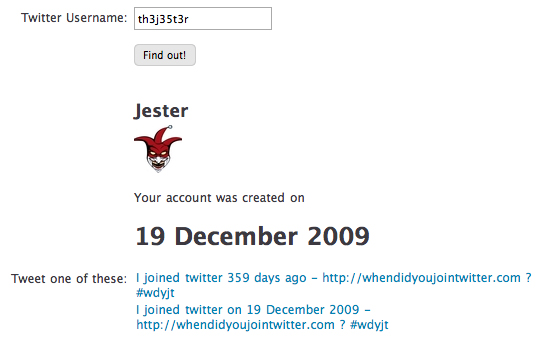
Source: whendidyoujointwitter.com, an online utility created by Neville Ridley-Smith.
th35t3r has denied being Robin Jakcson (rjacksix) as well:

Source: twitter.com/th3j35t3r
“Holy imposter Batman!”
On November 30, 2010, an imposter claiming to be th3j35t3r emerged on Twitter. The imposter used a very similar username: th3j3st3r. Note the subtle difference in which the imposter used an “s” in replacement for the “5”. He had to do this because usernames are unique on Twitter. Once a particular username has been registered, it cannot be used by someone else. Slight variations, however, are allowable as are duplicates of the Name field in a user’s profile.
The imposter used the same name in the Name field of his Profile as the real th3j35t3r. He also copied the real th3j35t3r’s Bio and Picture in his Profile:

Source: twitter.com/th3j3st3r
Other than the username, there was another significant difference: the imposter listed www.th3j35t3r.net in the Web field of his Profile.
According to Network Solutions WHOIS, th3j35t3r.net was registered with domain privacy on December 1, 2010:

Source: Network Solutions WHOIS
The imposter directed www.th3j35t3r.net to a wordpress.com blog that used the same theme (Greyzed) as the real th3j35t3r. (The imposter’s blog has since been deactivated and/or deleted.)
The imposter then posted the following blog entry:
So much for being quiet around here. The fire is starting to stir.. as many of you already are aware my door was kicked in and all of my equipment was seized. The weird thing is it was the local sheriffs office not the government. Hmmm..
In the mean time, my email and WordPress accounts are probably jeopardized so I decided to launch on my own server since nothing can be trusted at this time. I still have copies of all utilities, code, and web backups.
I am trying to raise money from my supporters for attorney fees. If I can raise the required $10k, I will release XerXes along with a port to Win32.
I will keep everyone posted as things start to unfold. I am not sure whats going to happen, no charges have been filed as of yet. Thanks for all your support! Don’t forget, Follow the new ‘th3j35t3r‘ Twitter!
On his dummy blog, the imposter included a link to gofundme.com for online donations:

Source: Crabbyolbastard Ruminates
In addition to trying to fleece some cash from unsuspecting suckers, it seems as though the imposter was also trying to stir up media attention and get federal agencies engaged in a hunt for th3j35t3r with a threat of porting XerXes to Windows and releasing it to every skiddie on the Internet to use indiscriminately to carry out DoS attacks.
On November 30, Mikko H. Hyppönen, the Chief Research Officer at F-Secure Corporation, tweeted that th3j35t3r had been raided:

Source: twitter.com/mikkohypponen
Robin Jackson (rjacksix), who follows Hyppönen on Twitter, replied:

Source: twitter.com/rjacksix
It was unclear what rjacksix meant by “cannot verify operational details”. The statement seems to suggest that the imposter could not verify “operational details” to rjacksix, which suggests that rjacksix and th3j35t3r had shared knowledge. This would leave only three options: 1) rjacksix was lying and has no knowledge of any of th3j35t3r’s “operational details”, 2) rjacksix is working with th3j35t3r and knows operational details that only he and th3j35t3r would know, or 3) rjacksix (Robin Jackson) and th3j35t3r have shared knowledge of operational details because they are the same person.
rjacksix then made an all-call to security professionals in which he suggested that the imposter was engaged in a social engineering (SE) attack on th3j35t3r:

Source: twitter.com/rjacksix
rjacksix then made several posts in a row that raised questions about the alleged police raid:

Source: twitter.com/rjacksix
While these were all relevant questions regarding the veracity of the alleged police raid, he soon after apologized:
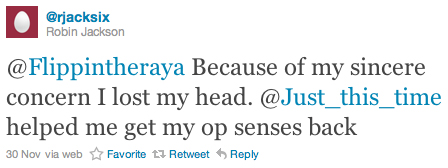
Source: twitter.com/rjacksix
Flippintheraya, Just_this_time, rjacksix, and th3j35t3r all follow one another on Twitter. In his posting, rjacksix refers to “op senses”, which was likely a shortening of “operation senses”. Again, this suggests his being involved in operations with th3j35t3r as well as with Flippintheraya and Just_this_time.
rjacksix then informed Hyppönen with “100% reliability” that the raid was faked by an imposter:

Source: twitter.com/rjacksix
Following this, rjacksix made a post containing a link to a posting on his website, dc406.com, entitled “th3j35t23r Social Engineering Scam” in which he stated:
“In a blatant attempt to use social engineering for either individual gain, or to discredit and break into the circle of people around the real jester…”
He also wrote, “th3j35t3r is dark, but probably safe. He has impeccable operational security. Numerous questions were asked of the imposter who immediately went silent when asked to answer simple questions.”
Further substantiating his claim that he and th3j35t3r are operating together, rjacksix posted the following tweets on December 1:


Source: twitter.com/rjacksix
While Anonymous’ assertion that Robin Jackson (rjacksix) is th3j35t3r is unsubstantiated, this is confirmation that he has at least been involved in some way with th3j35t3r’s ongoing operations. To what degree and in what manner is unclear. Based on his Twitter and website postings, however, it is clear that rjacksix is a big admirer of th3j35t3r and one could say that he quite literally he has been playing “Robin” to th3j35t3r’s Batman.
Anthony M. Freed has suggested that th3j35t3r himself was behind the imposter and the hoax of the police raid. So has Scot Terban, an information security professional who authors the blog Crabbyolbastard Ruminates.
“Was the The Jester (th3j35t3r) himself the instigator of reports that he had been the subject of a raid by law enforcement officials on Monday? That seems likely to be the case,” Freed concluded.
Terban, also believes that th3j35t3r instigated and was “in control” of the hoax the entire time:
“It’s my belief that Jester was in control [of the hoax] the whole time, but as to his motivations in doing this? I have no real clue other than perhaps this was a false flag to get people off of the trail,” wrote Terban on his blog.
Freed and Terban are most likely wrong in their individual assessments. A hoax that draws media attention and raises the specter of th3j35t3r porting and releasing XerXes on the Windows platform doesn’t seem to fit with th3j35t3r’s modus operandi and his attention to OPSEC.
Additionally, during the course of compiling this report, we’ve read all of th3j35t3r’s Twitter and blog postings, as well as various comments he has left on other people’s blogs. The “voice” of the writing in the imposter’s blog posting doesn’t sound like th3j35t3r; rather, it sounds like someone trying to sound like him and doing a very poor job of it. The real th3j35t3r sounds intelligent. The imposter, on the other hand, sounds stupid.
In a December 8 blog posting that addressed “The Imposter Saga”, th3j35t3r himself pointed out the imposter’s stupidity and obvious logic flaws:
“[The imposter] claimed that I had been arrested by errr the local Sheriff (lol) and since released without charge but still needed to raise (a measly) $10K for a legal defense fund.- PS you were released without charge – why do you need a defense fund?”
According to th3j35t3r, he contacted the imposter on Twitter via Direct Message (DM):
“I approached this person via DM and kindly pointed out that he has just made himself a huge target, especially by registering a domain name, and by clearly not having any kind of situational awareness, will be found, and they will think you are me. He immediately (not by my request) pointed his domain to this blog. Fool.”
In regards to the request for money and the promise to port XerXes to Windows and release it th3j35t3r said:
“As has been stated over the last 12 months many times. I do NOT require any financial donations, will never ask for any, and if, as in last week’s debacle, it ever again appears I have asked for donations, look carefully at the facts: It will not be me begging for cash. Ever.”
The Herd Mentality
One speculation raised in the #AnonymousDown IRC session is the possibility that th3j35t3r is not a single person, but a front created by the U.S. Government in order to carry out unattributable cyber-attacks. There is no hard evidence for which to substantiate this far-fetched claim; only circumstantial evidence that makes it of interest even though it gets cut to pieces when pressed against the sharp blade of Occam’s razor.
In a January 2, 2010 Twitter posting, th3j35t3r wrote, “Terrorists are utilizing internet technologies to recruit, propagate, and co-ordinate. I exist in shadow to disrupt their online activity.” If the th3j35t3r is a U.S. Government-sponsored operation carrying out cyber-attacks “in shadow”, it would be a secret, special access program that only those who were read-in to the program would know about.
While it is easy and common for people to manufacture all kinds of elaborate government conspiracies in an attempt to explain all sorts of world phenomena that they do not understand, the creation of a secret government operation that utilized manufactured identities, online personas, media manipulation, misinformation, and deception is not beyond the realm of possibility.
U.S. intelligence services have a long history of creating and executing outlandish and complex operations, such as the CIA’s creation of a fake science film to sneak six Americans out of Iran in 1979 during the Iranian Revolution. Such clandestine operations in cyberspace would be far less risky and dangerous than actual field operations. Clandestine cyber-operations would also take far less resources. A small team of subject matter experts could accomplish a lot in very short order. Additionally, OPSEC would be vastly improved. As the emerging saga of Cablegate has demonstrated: secrecy is inversely proportional to the number of people in-the-know.
A possible down-side of such a compartmentalized operation is that it could work at cross-purposes with other U.S. intelligence operations. For example, th3j35t3r’s disruption of jihadist websites and discussion forums could dampen ongoing intelligence-gathering efforts by the NSA. The resulting disruption of ongoing communications and the possible scattering of participants could effectively dry-up the gathering of actionable intelligence.
th3j35t3r has refuted this notion on Twitter in an exchange with Leah Farrall (allthingsct), a former senior Counter Terrorism Intelligence Analyst with the Australian Federal Police (AFP) who authors the blog All Things Counter Terrorism.

Source: twitter.com/th3j35t3r
While his DoS attacks against suspected jihadist websites are certainly disruptive, th3j35t3r advocates that these attacks have a “herding” effect.
“By NOT hitting certain sites, and hitting others hard, I am ‘herding’–people give up easily when a site is constantly up and down, and move on to a more reliable one,” th3j35t3r said in his interview with Welt Online. “So it creates a funnel-effect–funnelling terrorists and potential terrorists away from peripheral sites and into a smaller space that is easier to monitor.”
If that is indeed the case, th3j35t3r would be aiding ongoing intelligence-gathering efforts by narrowing down the number of suspected jihadist websites and discussion forums monitored by U.S. intelligence services.
However, there is also the possibility that his efforts have had a chilling effect and result in herding jihadist communications out of the clear and receding into the digital underground of the darknet.
According to Terban, th3j35ter’s DoS attacks on jihadist websites have had little effect at all.
“Sure he was pissing off some in the intelligence community,” wrote Terban, “but for the most part people ignored him because he was not performing any kind of substantive attacks that effected change. The jihadi’s kept on talking on the same sites that they mirrored.”
A “Frosty” Conclusion
The tagline for th3j35t3r’s blog is “Stay Frosty My Friends”. So far, this has been the case as attempts to uncover th3j35t3r’s identity have all gone cold. While Robin Jackson (rjacksix) of Helena, Montana has publicly claimed that he and th3j35t3r “have worked together” and share “operational details”, it is unlikely that Robin Jackson is th3j35t3r himself. At most, rjacksix and others have provided some level of operations support for th3j35t3r.
While unsubstantiated, it is unlikely that no one inside the U.S. intelligence community, the Department of Defense, or law enforcement has no knowledge as to th3j35t3r’s true identity given his stated military background and the fact that he posses such a demonstrably powerful and effective cyber-weapon as XerXes, which could wreack havoc on the World Wide Web if the code base were indeed released into the “skiddie” community. At a minimum, th3j35t3r is likely receiving tacit support from the U.S. Government for his ongoing operations against suspected jihadist websites and most recently wikileaks.org.
And if th3j35t3r is not an individual at all but rather a persona created as a front for a secret government program to carry out unattributable cyber-attacks against specific targets, it is highly unlikely that we’ll ever know the truth about that–well, unless someone on the inside leaks evidence of the existence of such a program via an organization like WikiLeaks.
Meanwhile, the identity of th3j35t3r as an individual, a group, a secret government program, or otherwise remains unknown and he remains “crack on” as he has commented with his DoS campaign against suspected jihadist websites.
###


























